From clothing tags to fridges, a myriad of devices are increasingly connected to the internet as part of the internet of things (IoT). Often, these devices exchange important personal or financial information over the internet through information and communication technology (ICT) devices. This requires built-in hardware identification technology to prevent malicious attacks.
Hardware identification technology using a circuit function known as Physically Unclonable Function (PUF) offers greater security for ICT devices. PUF outputs a random number value, generating a unique hardware fingerprint. This can be used for a host of security purposes such as identification, authentication and key generation.
However, PUF is sometimes unstable and inefficient because it utilizes minute differences in uncon-trollable hardware details. Now, a research group from Tohoku University, led by Professor Naofumi Homma, has overcome this problem with the discovery of a new technique for identifying hardware fingerprints with PUF in the most efficient manner possible.
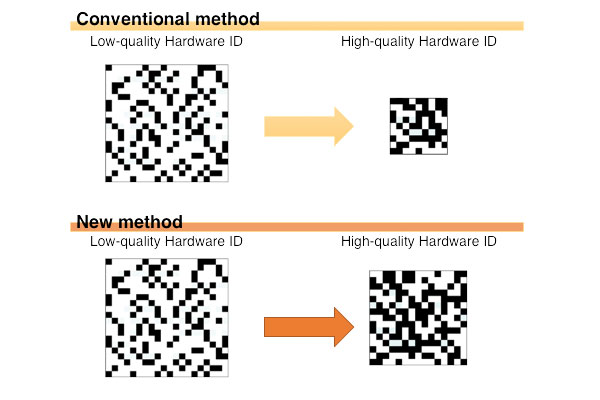
The new technology succeeded in eliminating the bias of PUF output (ratio of 0 and 1) in an efficient manner as shown in Fig.1. This prevents the degradation of security and makes it possible to use vari-ous PUFs securely. The new technology also makes it possible to reduce PUF size by more than 50% of the current level (Fig.2).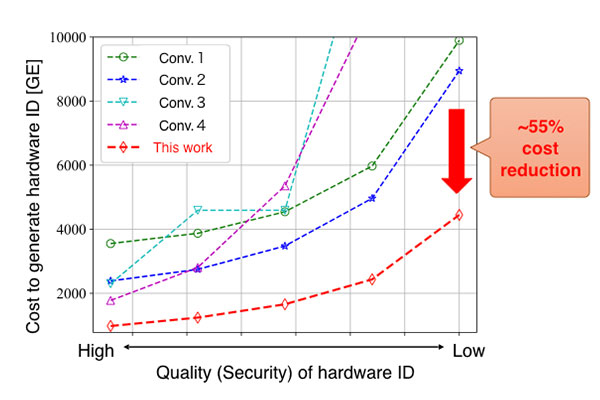
“With this achievement, it has become possible to include hardware identification technology even in ICT devices that have tight resource or energy constraints; therefore, enhancing the security of the next generation IoT,” said professor Homma.
The researchers will now seek to put this technology into practice by embedding this hardware identi-fication scheme into actual IoT devices
Professor Ueno, co-researcher of the study, announced their results on September 16, 2020, at the In-ternational Conference on Cryptographic Hardware and Embedded Systems 2020 (CHES 2020). The conference was hosted by the International Association for Cryptologic Research (IACR).
- Publication Details:
Title: Rejection Sampling Schemes for Extracting Uniform Distribution from Biased PUFs
Authors: Rei Ueno, Kohei Kazumori, and Naofumi Homma
Journal: IACR Transactions on Cryptographic Hardware and Embedded Systems
DOI:







69cba92a-ea8f-44ce-bfec-4dab42e7e2c0.jpg?sfvrsn=a6461a8c_1)
